Avast Business CloudCare Antivirus
MORE THAN 50 SCREENS!
Avast antivirus
The Avast agent is the software that is installed on the devices and contains the protection functionality, which is configured from the administrative website. Many of these tools can be controlled or restricted from the administrative website and may even deny access to users to prevent the modification of functions or prevent the uninstallation of the Avast agent. The following list shows all the available functions that can be configured in the devices (computers, laptops, servers).
- Antivirus
- Web Shield
- Behavior shield
- firewalls
- Antispam
- Electronic Choir Shield
- Browser Cleaning
- Wifi Inspector
- VPN Secure Line
- Legitimate Website
- Testing environment
- Recovery disk
- Data Destroyer
- Exchange protection (for servers)
- SharePoint protection (for servers)
- Remote Desktop Access
Administrative Website
The Avast Business Cloudcare administrative website has tools for configuring the devices that the Avast agent has, here you can select the functionalities you want to run on the devices. In addition, it has a series of utilities such as: the creation of additional users to give access to the remote desktop, generate reports, configure alerts, and centrally monitor the devices.
- Dashboard
- Installer
- Avast Agent
- Alerts
- Devices
- Antivirus
- Sandbox
- Default Policies
- Antispam
- Browser Cleaning
- Email Shield
- microsoft Exchange
- Microsoft Sharepoint
- firewalls
- Web Shield
- About
- Remote Desktop Access
Dashboard
The Dashboard is a centralized control panel that provides you with an overview of your network, showing infected devices, devices that require attention, alert summary, summary of browsing activities, devices that need updating of the antivirus database and a general description of them. The graphs give you a global vision of detected alerts and allow you to keep track of them. It can also monitor memory usage, hard drive usage, communication problems, as well as verifying the correct installation of the antivirus.
Installer
The Avast Business Cloudcare installer allows you to choose between generating installation files for PC or Mac computers, generating an installation link, an executable file, or if you want to do a global installation with active directory. All these options contain the components that will be installed on the different devices, these components are: Antivirus, Web Shield, Behavior Shield, Firewall, Antispam, E-Mail Shield, Browser Cleaning, Wifi Inspector, Secure VPN Line, Site Legitimate Web, Test Environment, Recovery Disk, Data Shredder, Exchange Protection (for servers), SharePoint Protection (for servers), Remote Desktop Access (optional).
Avast Agent
The Avast agent is the software that enables communication between the device and the administrative web. Many of these tools can be configured from the administrative website, and may even restrict user access to prevent modifying any function or prevent the Avast agent from being uninstalled. In addition, through this communication with the administrative website, you can define functions such as: days to run full scans, configure the use of a proxy server to perform updates, install or uninstall Avast Antivirus modules and restart or shut down a device. If you have the version with Premium support you can communicate remotely from the Avast website with the PC or MAC device. The Avast agent is also a service that sends monitoring information to the administrative website, such as: available disk space, processor usage, detection of a virus and if it was removed or quarantined. Another great feature is that once the Avast Business Cloudcare Agent is installed on one device, you can automatically install it on other devices on the same active directory network as well. This helps you speed up the installation process on PC or MAC devices on a network without having to go through each device to install. The Avast agent also sends information to the administrative website of which devices are on or off, the device’s IP, device type, operating system, and the device log.
Alerts
In the alerts panel you can configure parameters to monitor network devices, for example, you can configure the reception of alerts if the capacity of the hard disk has been reached.
Some of these alerts are: Outdated Virus Definitions, Device Needs Reboot, Threat Detected, Failed Service Update, Blocked URL Access Attempt Detected, CloudCare Uninstalled, Service Installation Failed, Device Not Communicating, Antivirus Protection Disabled, Disk capacity reached, memory utilization reached, virus scan delayed, service will expire, CloudCare installation successful, Windows service started, Windows service stopped, and more.
You have the option of creating different alerts for different groups of devices. For example, you could create alerts for servers, for PC’s, for Mac computers.
Devices
The devices panel shows you a list of all the devices where you have installed Avast Business CloudCare antivirus. This list includes devices that may not necessarily be on the same network or physical facility.
Also in this panel you can create different groups of devices to better organize your equipment. You can also view device IP details or start a remote session if you have the remote access module installed.
Other available functions are: the ability to be able to shut down or reboot a device, send updates, initiate a virus scan remotely, select the installation of other components that have not been installed.
Antivirus
Avast Business CloudCare antivirus is a complete suite of protection for PCs and other devices, the application in its latest version, has numerous multi-functional security tools to protect your PC. From the administrative website you can configure options such as scan frequency, activate or deactivate the antivirus on a specific device or group, configure the update frequency, create exclusions of directories that you do not want to scan, configure the scanning behavior of programs that are executed on the device, exclude file scanning by extension (example: .bat, .png, exe, .zip, ppt, etc).
Testing environment
If you have dangerous files and want to open them, use our virtual “safe space”, where you can safely run any file outside of the rest of your PC. You simply select the file you have downloaded and Avast Business CloudCare will run it in an environment isolated from the rest of your computer. Also from the administrative website you can configure the behavior and how to handle these files that you want to run in the test environment. Other functions that can be managed from the administrative website is the exclusion of functions such as: cookies, bookmarks or browsing history. You can also configure the restriction of the applications that you want to be executed in the test environment, such as, for example, that they do not have access to the internet or important directories.
Default Policies
The default policies are controlled from the administrative website and their objective is to prevent the user from modifying functions configured in the agent / antivirus installed on the device. In addition, you can create the number of policies you need and assign them to groups of computers as you like. For example: you could create policies so that on certain devices the scans run at a certain time, exclude scan directories on certain groups of computers, open ports on certain groups of computers, block access to certain websites on certain devices and on certain computers. others do not, perform scans to specific browsers, specify functions for servers, desktops, laptops, Mac’s. You can also decide the action to take based on the results of a scan, such as deleting infected files or quarantining them. Other settings can be made such as assigning absolute control to the device user over the local antivirus settings, creating rules in the firewall, adding emails to the Antispam service to be blocked or excluded, among others.
Antispam
The best way to mitigate the risk is to eliminate it completely: prevent dangerous phishing emails (and annoying spam) from reaching your inbox and those of your employees. The administrative website gives you the option to configure the actions to take when the Avast system detects emails that may be spam. For example: you can decide if you want the origin of the emails to be marked with the word SPAM and also if you want these messages to be moved to a junk directory automatically. Additionally, you have the option to add emails or domains that you do not want to be scanned or if you want to automatically block them.
Browser Cleaning
Unwanted plug-ins and unnecessary browsing data can affect employee performance or compromise data. Keep your system up and running safely and quickly with regular browser cleaning. With the administrative web you can configure if you want the Avast agent to be aware of the files that are downloaded in the temporary directories and move any type of file that could compromise your computer in the future. In addition, it helps you remove unwanted browser bars that have poor ratings and that may compromise the privacy of your users.
Email Shield
Scans both incoming and outgoing email messages to ensure they don’t contain any malware. Unlike ANTISPAM, the email shield inspects email content and represses content that could compromise your computer, such as links to infected websites, malware, viruses or links to suspicious websites. In addition, from the administrative website you can configure what type of files are scanned and which ones are not. Another function available is to define whether the Avast agent scans incoming emails, outgoing emails or both, and insert a message in the email to let the user know that Avast has found something suspicious. From the administrative website you can also configure the sensitivity of the electronic shield module as low, normal, high scan or disable it completely.
microsoft Exchange
The Microsoft Exchange Web Shield is designed to be installed on an Exchange server. Scans and filters email messages that may contain malicious attachments or dangerous links, to prevent internal communications from being threatened by malware. From the Avast CloudCare administrative website you can create policies for servers that have Microsoft Exchange and in this way you can maximize the use of the processor on devices that are not Exchange servers. Some of the settings that you can define in the administrative web are: scan incoming messages in the users’ mailbox or before they reach the transport level tray. You can also configure actions such as marking the message with a warning or erasing it entirely. In addition, the Exchange module can try to decompress packed files to be reviewed before sending them to the user’s tray, or lock them and send a note file with the information of the file that was locked, so that the user knows that the mail contained an attachment but was blocked by the Avast Exchange Protection service.
Microsoft Sharepoint
Scans all files uploaded to the shared storage space to prevent malware from compromising data.
From the Avast CloudCare administrative website you can create policies for servers that have Microsoft SharePoint, and configure the respective settings so that users do not have access to infected files or replace these files with a warning. In addition, it has the option for the Microsoft SharePoint module to decompress packaged files in a safe environment and scan them to verify that there are no infected files within the compressed file.
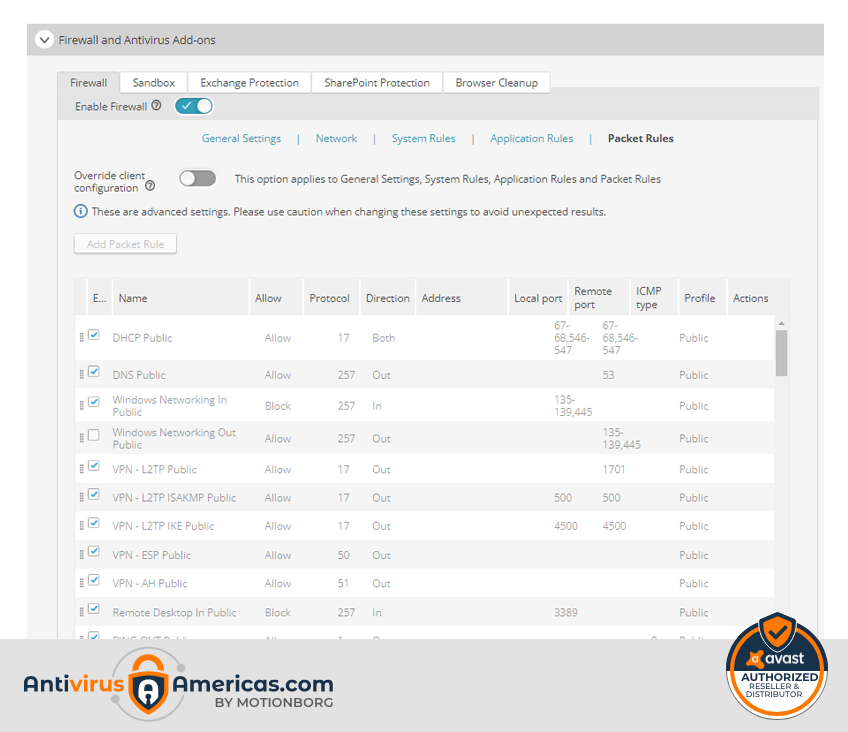
firewalls
If you lock the doors of the business, you have to do the same with the network. To do this, we offer you a powerful, customizable Firewall that stops unwanted visitors.
The Avast administrative website gives you the option to configure groups of computers that run services that can be blocked, or to give access to a program to connect through a specific port on the computer. This is a great feature for restricting access to unwanted programs that could compromise user devices and thus maintaining complete control of the services running on your network. The Avast administrative panel allows you to configure the policies by which devices are governed, which cannot be modified by users. It also has the option of providing absolute control to the user of what you deem appropriate. Another great feature available is being able to bypass a device so that it cannot communicate with other computers on your network. This function is very useful when you have an employee who needs to carry out research or searches through the Internet, but does not want to compromise his network to a virus or some malicious program.
Web Shield
Check website URLs and certificates to ensure they are secure before a network connection is established. From the administrative website you can configure what type of browsers the agent must protect, and what type of protocol it must protect, such as HTTP or HTTPS. In addition, it gives you the opportunity for the user to be alerted about the files they are downloading when they have low reputation.
Another excellent function is to be able to configure the type of files to be scanned, such as .doc, .exe, .jpg, etc. and what action to take, such as blocking them, cutting connection, putting them in quarantine, among others. Also, it allows you to configure the sensitivity of the scans or turn them off completely.
The web shield allows you to block websites that you do not want to access such as: Facebook, YouTube, Instagram, banks, or pages with adult content.
Additionally, you can configure the reception of reports from blocked websites that have tried to access from devices on your local or remote network, regardless of where the device is located.
About
The Avast Business CloudCare administrative website has an automated reconfigurable reporting system, which you can configure to receive email or SMS alerts. Some of the alerts that you can configure are:
- Outdated virus definitions
- Device needs to reboot
- Threat detected
- Service update failed
- Access attempt to blocked URL detected
- CloudCare uninstalled
- Windows service blocked
- Failed service installation
- The device is not communicating
- Antivirus protection disabled
- Disk capacity reached
- Memory utilization reached
- Overdue virus scan
- The service will expire
- Successful CloudCare installation
- Windows service started
- Windows service stopped
…and many more.
Remote Desktop
With our optional Premium package, you will have the facility to enable your employees or internal technical support department, the option to connect to any computer that has Avast Business CloudCare installed. You can allow access to any of your workers to a group of computers or to a specific one, and at the same time your technology department can use this module to provide support, to be used by a human resources person, the owner of the company. , or to initiate and maintain remote conferences, view and share the remote device’s screen. In addition, from the Avast administrative website you have the option to cut access completely or uninstall the remote access system if it is not applicable for certain personnel.
REMOTE DESKTOP (REMOTE ACCESS) allows you to take full control of all your PCs from anywhere in the world. With the CloudCare agent, connect securely to any device. This tool works remotely, solves problems, performs tasks, restarts computers, transfers files, and you will also be able to chat with users. Here is a list of remote desktop features:
- Work remotely
- Transfer files
- Record screen sessions
- Text, audio and video chat
- Draw on screen
- Virtual pointer
- Share remote screen
- Share local screen
- Dual monitor support
- Print function
- View system resources
- Remote computer restart
Behavior shield
Malware can hide deep within the programs you use. The Behavior Shield monitors them all for suspicious activity to prevent attacks.
It is like having a policeman on your computer who is constantly inspecting dangerous behavior, such as files that can encrypt your data, or programs that can erase your information whether they come from the internet or your local network.
In addition, artificial intelligence technology can detect programs that may be trying to steal your passwords stored in your browsers or your computer and defeat the program that tried to compromise your information.
The Avast Business CloudCare administrative website allows you to configure the behavior to follow, once a malicious program is detected, so that it cannot cause any of the aforementioned problems.
VPN Secure Line
Always use private connections on all networks or wi-fi connections used by your employees to prevent other people from seeing and stealing your identities or business data. Avast SecurelineVPN. encrypt internet connections. It also allows you to connect to different proxy servers on the internet so that your browser is not inspected by any restricted network. It also allows you to access websites that are not allowed in some countries, by creating a tunnel with secure servers in different parts of the internet, which serve as bridges and tunnels to navigate safely and without restriction. An example would be to watch television programs on websites that are not accessible if you do not have your internet provider account or connect to websites or services in other countries which are blocked by your local service.
Real site
Fake websites are one of the tools that hackers use the most to get people to provide their personal information with deception. Avoid entering these sites and protect your employees. Stay protected from sites that can steal your data.
The Avast Business CloudCare Antivirus system alerts you if a website is compromised by a hacker or if the site is not the real website of a bank or government institution. This is a system that does not require configuration from the Avast administrative website, as easy as enabling the real site module to protect your computer.
Recovery disk
The recovery disk is a function of the local Avast agent, it allows the user to create a USB drive or CD with the Avast Business CloudCare program, which he can use to scan the computer without having to run the operating system. Simply create the USB drive or CD and insert it into the computer and the program loads its own operating system, in order to scan files or places on your hard drive that if the system had been running it would not have been able to scan files that were in use.
With a special external disk, you can run malware scans before the operating system boots. In this way, malware that is found in the recesses of the system that otherwise could not be found can be discovered.
This is a module that can be enabled for a group of devices from the Avast Business Cloud Care administrative website.
Data Destroyer
Deleted files can be easily recovered. Destroy confidential documents that contain financial information or customer and employee data forever.
The Avast Business CloudCare program allows the user to permanently erase those sectors of the disk that contain data that an operating system generally does not erase. This is excellent for companies such as law offices or government companies, which have sensitive information and once deleted, no one should have access to it.
This is a module that can be enabled for a group of devices from the Avast Business Cloud Care administrative website.
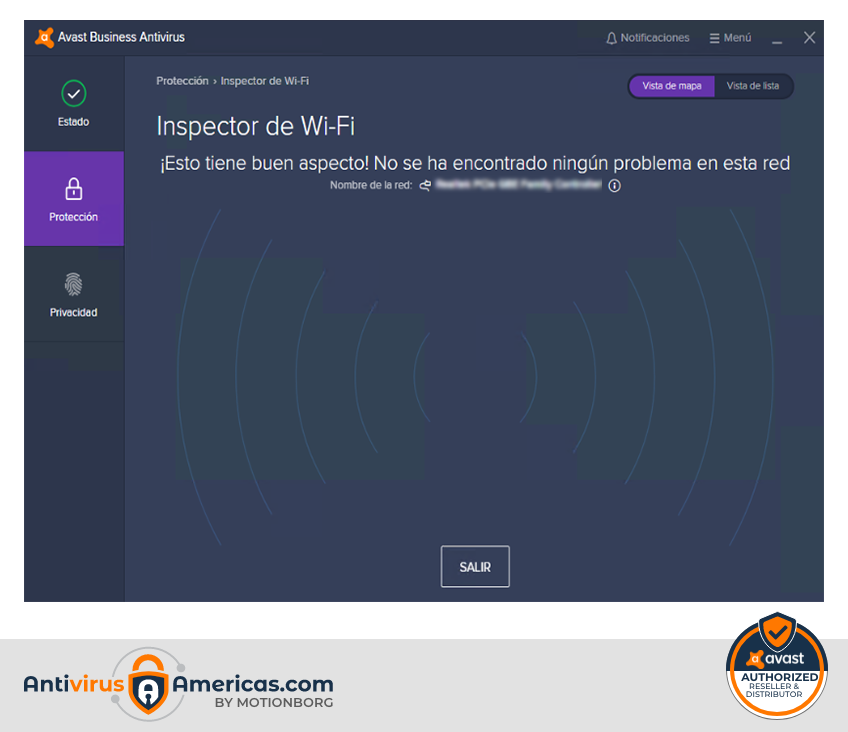
Wifi Inspector
Cybercriminals now have more means than ever to sneak into a network. Use our network analysis tool to find and strengthen weak spots that may pose a risk.
Avast’s WIFi Inspector allows you to scan your physical network for vulnerability holes that may be exposed by bad wireless network configurations.
It also issues a report of all the devices on your network, and the possible problems that may cause open doors to the internet through a poorly configured wireless network.
This is a module that can be enabled for a group of devices from the Avast Business Cloud Care administrative website.
Need Help or Have Questions?
We are here to provide any help you may need. For technical problems or help with installation, use our SUPPORT form to open a support ticket. If you have product questions or if you need information about the product, please use this contact form or if you prefer to speak to a representative call us at (305) 302-5543. If you want us to call you back, specify that you want us to call you on the following form, and include your phone number and we will be happy to answer any question you may have. If you have a current subscription please include your order number.